TerraMaster is a relatively new company specializing in network attached storage and direct attached storage solutions. The majority of TerraMaster NAS solutions are ARM64 and Intel-based boxes aimed at the home and SOHO users. TerraMaster’s OS (TOS) is based on Linux. At this time, TOS 4.1 is the current version of the OS.
TerraMaster advertises secure AES encryption with unspecified key length through the entire range of its current NAS devices. This time around, we’re dealing with folder-based encryption that runs on top of the open-source encrypting file system eCryptfs. TerraMaster’s implementation of data encryption is extremely simplistic and lacks any sort of management for either the encryption key or the encrypted data.
Abstract and Summary
TerraMaster implements folder-based AES encryption with a single, fixed, unchangeable encryption key based on the user-provided password. The company does not specify the length of the key used for AES encryption. A 42-byte (336-bit) encryption key file can be manually exported for backup purposes. Users can unlock encrypted volumes by either typing the original plain-text password or uploading the encryption key.
TerraMaster has never documented any technical details about the underlying encryption mechanisms.
Encryption key: plain-text password or key file (must be manually exported while the encrypted share is mounted and unlocked).
The original password is used as Media Encryption Key. The concept of Key Encryption Keys is never utilized here; as a result, users cannot change their encryption password at all. In addition, TerraMaster OS does not have provisions for encrypting existing data or permanently decrypting encrypted shares. Any changes to encryption require deleting and re-creating shares and filling them up with data.
The entire encryption scheme lacks any sort of technical documentation.
Test Bench
We analyzed a TerraMaster F2-220 device based on a quad-code ARM64 design. A non-SED WD Red HDD was used to set up the NAS perform the analysis. The NAS was running on the latest available version of TOS 4.1.
TerraMaster: Folder-Based Encryption
TerraMaster uses folder-based encryption based on eCryptfs, an open-source stacked cryptographic file system. Detailed information on eCryptfs is available here. This is the same encryption scheme as used in consumer Synology NAS devices. However, while Synology properly documents the restrictions of folder-based encryption, TerraMaster does not. As a result, the user finds out about the fact that encrypted file names are restricted to 143 Latin characters in a hard way by getting a write error when attempting to store a file with a name that is longer than permitted. Using Asian characters makes the possible file names even shorter.
From the point of view of a normal consumer, TerraMaster’s implementation of encryption is not just restrictive; it’s restrictive by surprise since no advance warning is given and no documentation is available about it.
Once the encrypted share is created, users cannot change the encryption passphrase.
Encrypting
Users can only encrypt newly created, empty shares. Encrypting an existing share is not possible. One must first delete the encrypted share, create a new one while selecting the encryption option. As a result, encrypting shares with existing data is not supported.
The good thing about this encryption scheme is the ability to create multiple shares, each with its own unique password. If there are multiple users, each user can encrypt their personal share with their own password. However, the complete inability to change the encryption password makes this approach dubious in the grand scheme of things.
Creating an encrypted share
The first step is creating a new share:
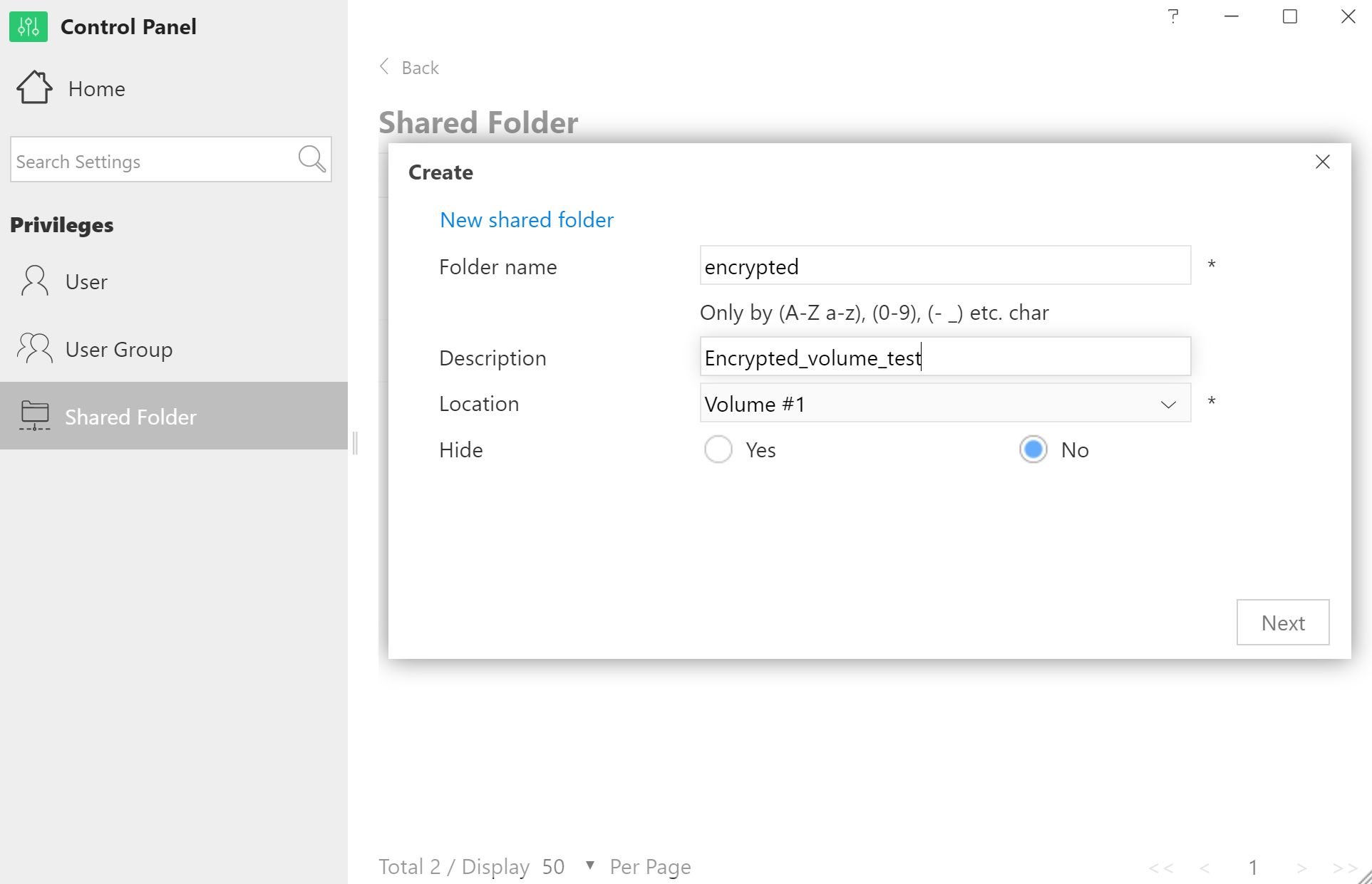
The “Encrypt this shared folder” box activates the encryption. The encryption feature requires a password, which is used as an encryption key. There are no obvious limitations (minimum or maximum) to the length of the password or supported character sets.
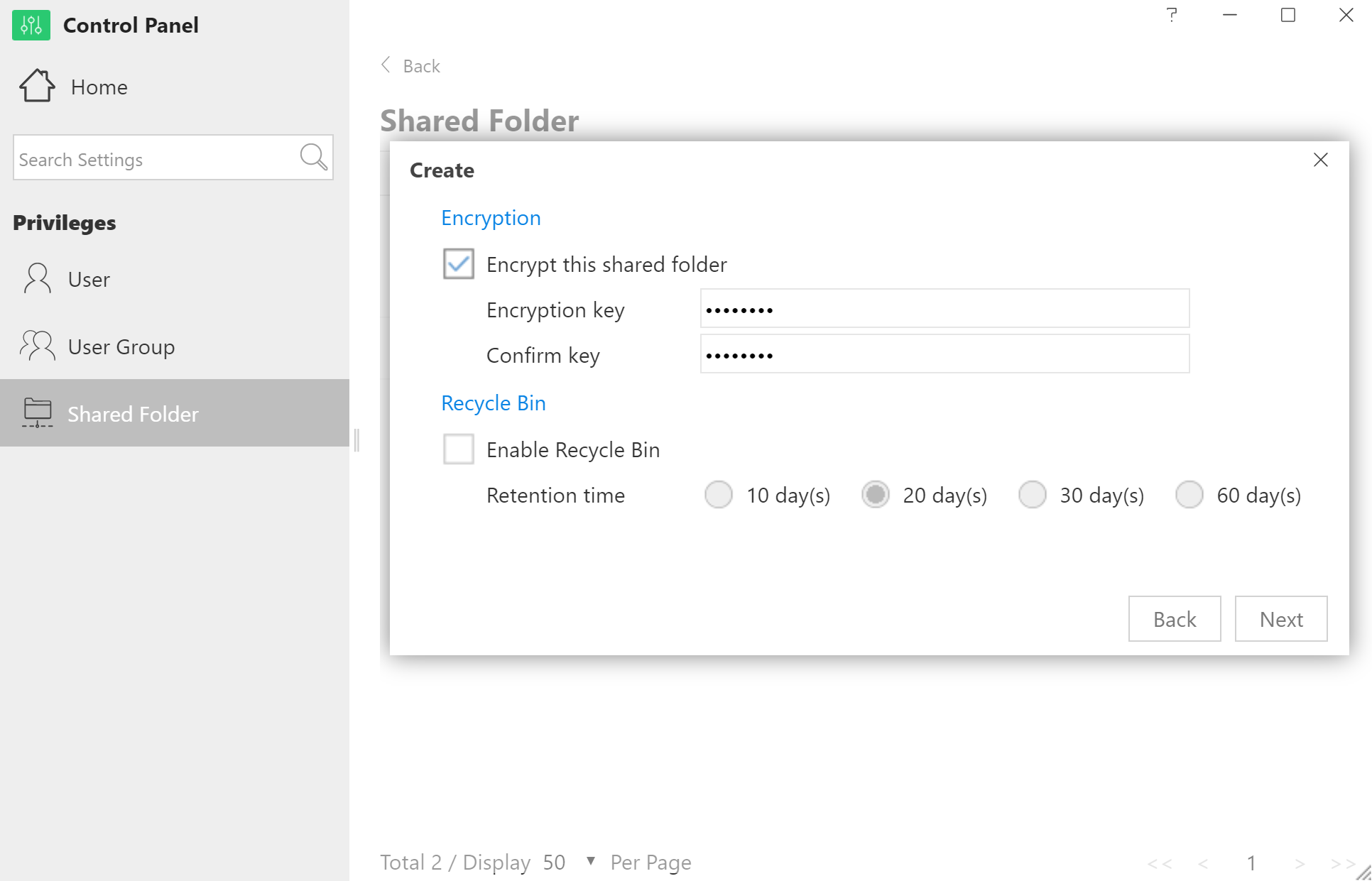
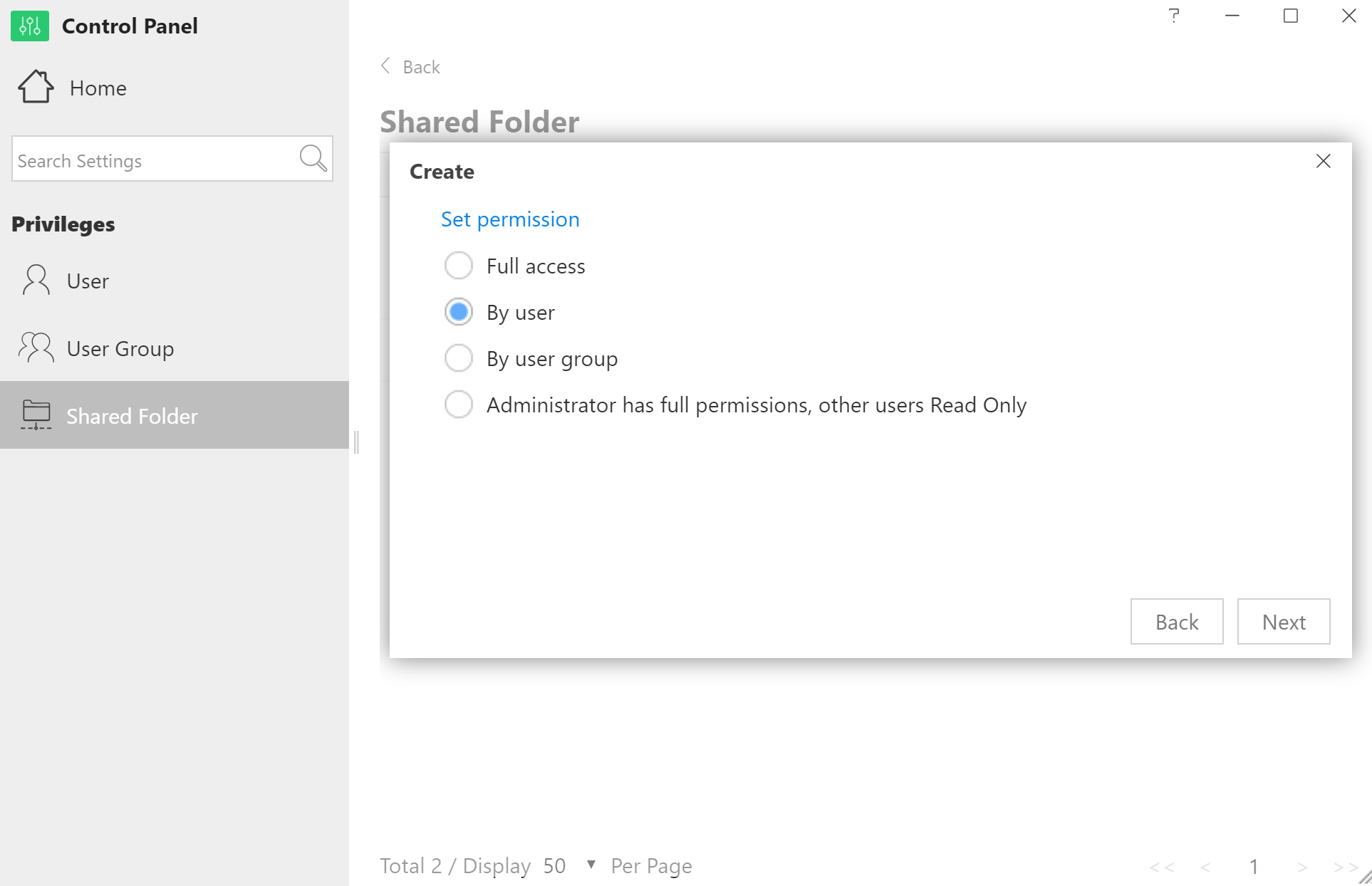
The process is concluded after setting access permissions and confirming settings:

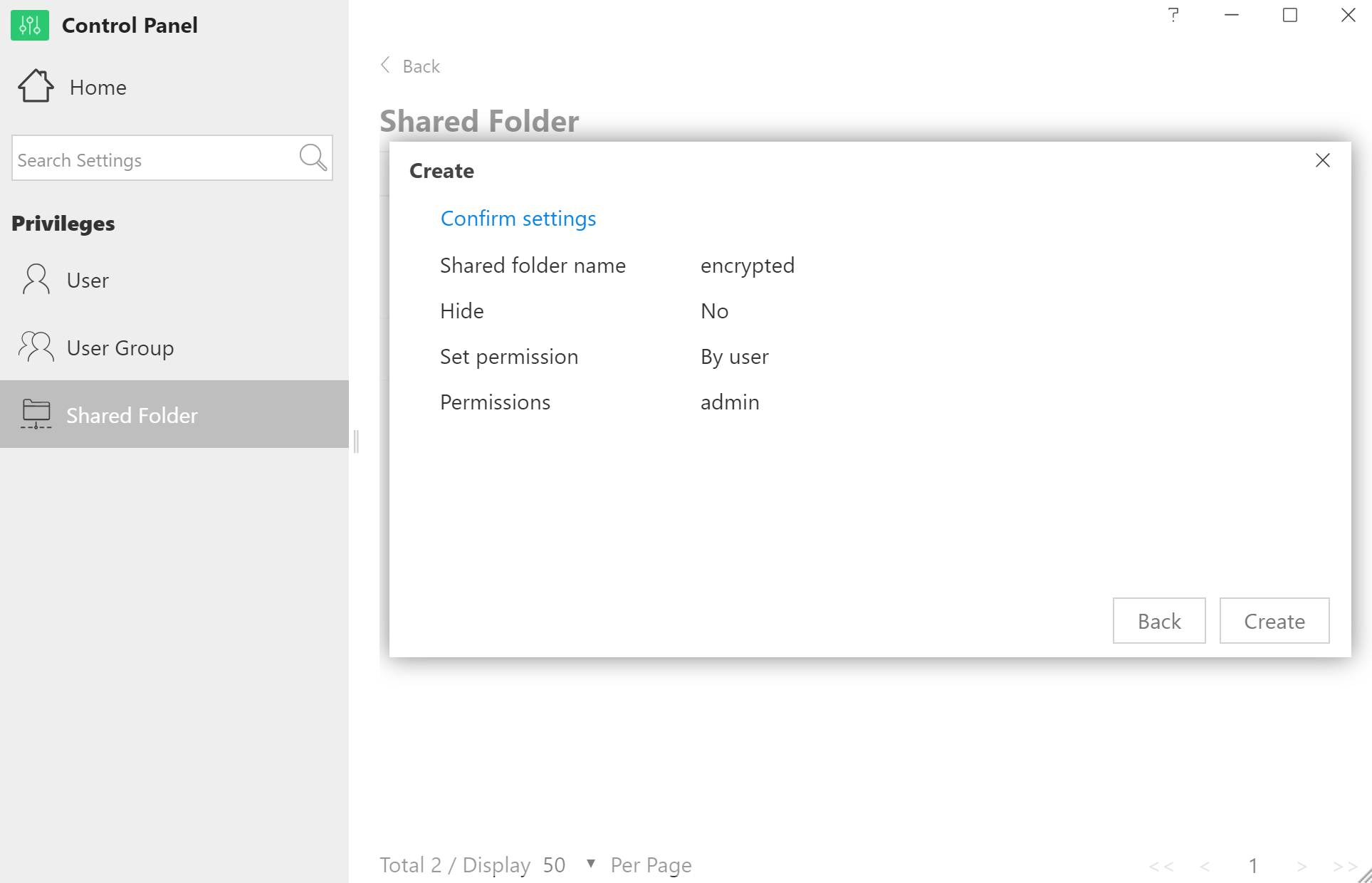
The encrypted share is created and mounted. Note the “lock” icon:

Exporting the encryption key
Pretty much the only thing users can do with their encryption key other than using it for mounting shares is exporting it to a file.
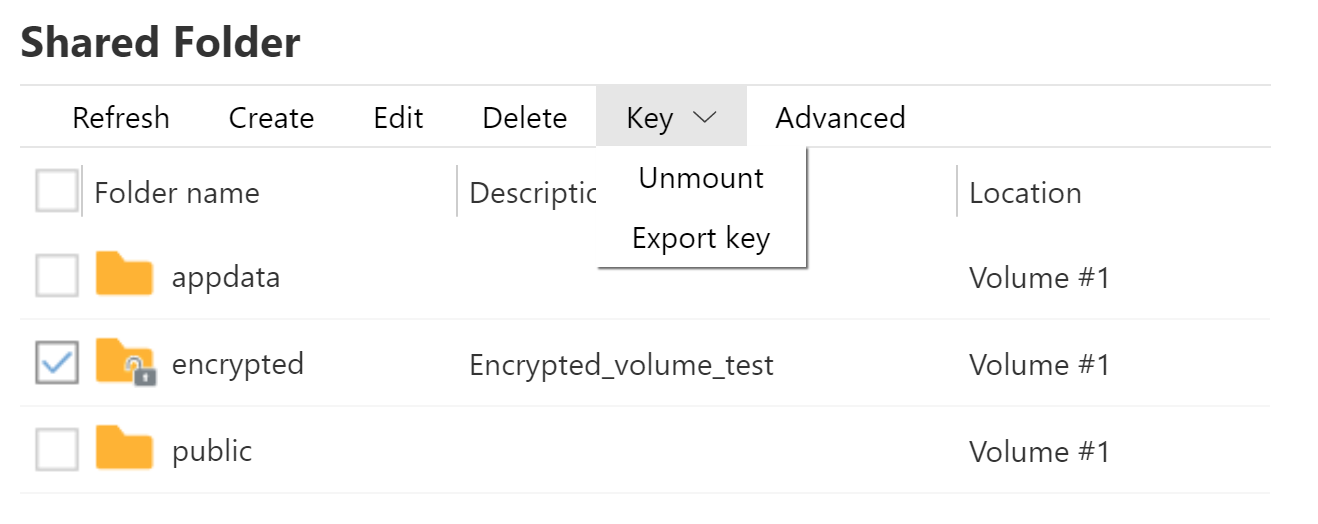
In order to export the key, users must re-enter their encryption password:
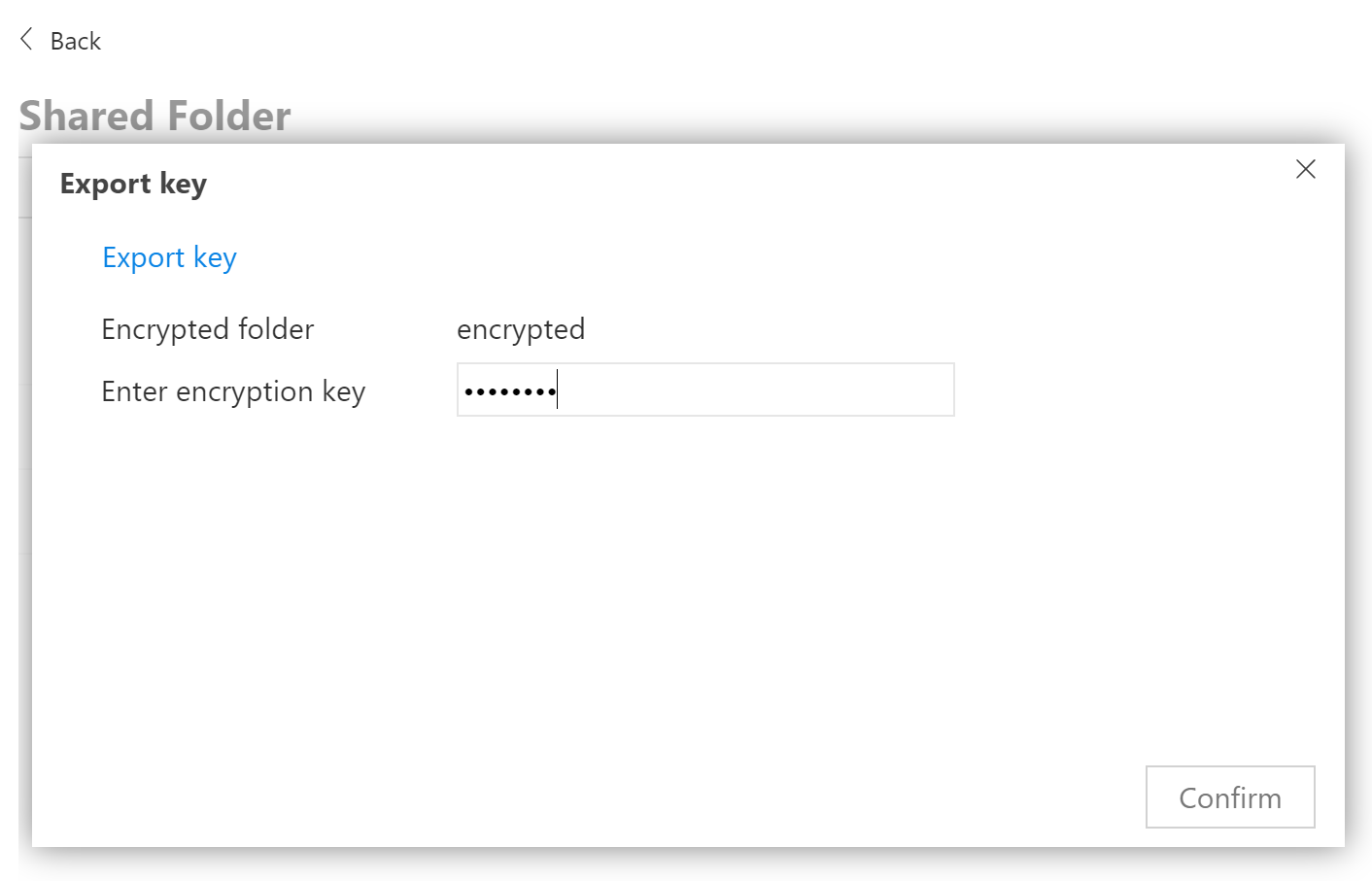
Mounting encrypted shares
The encrypted volumes can be only mounted manually. Users must log in to the TOS Web UI, click on the encrypted share and use the Mount command. There are no auto-mount options available, and there are no vulnerabilities connected with the improper storage or handling of encryption keys.
The following two options are supported.
- Mounting with the original plain-text password.
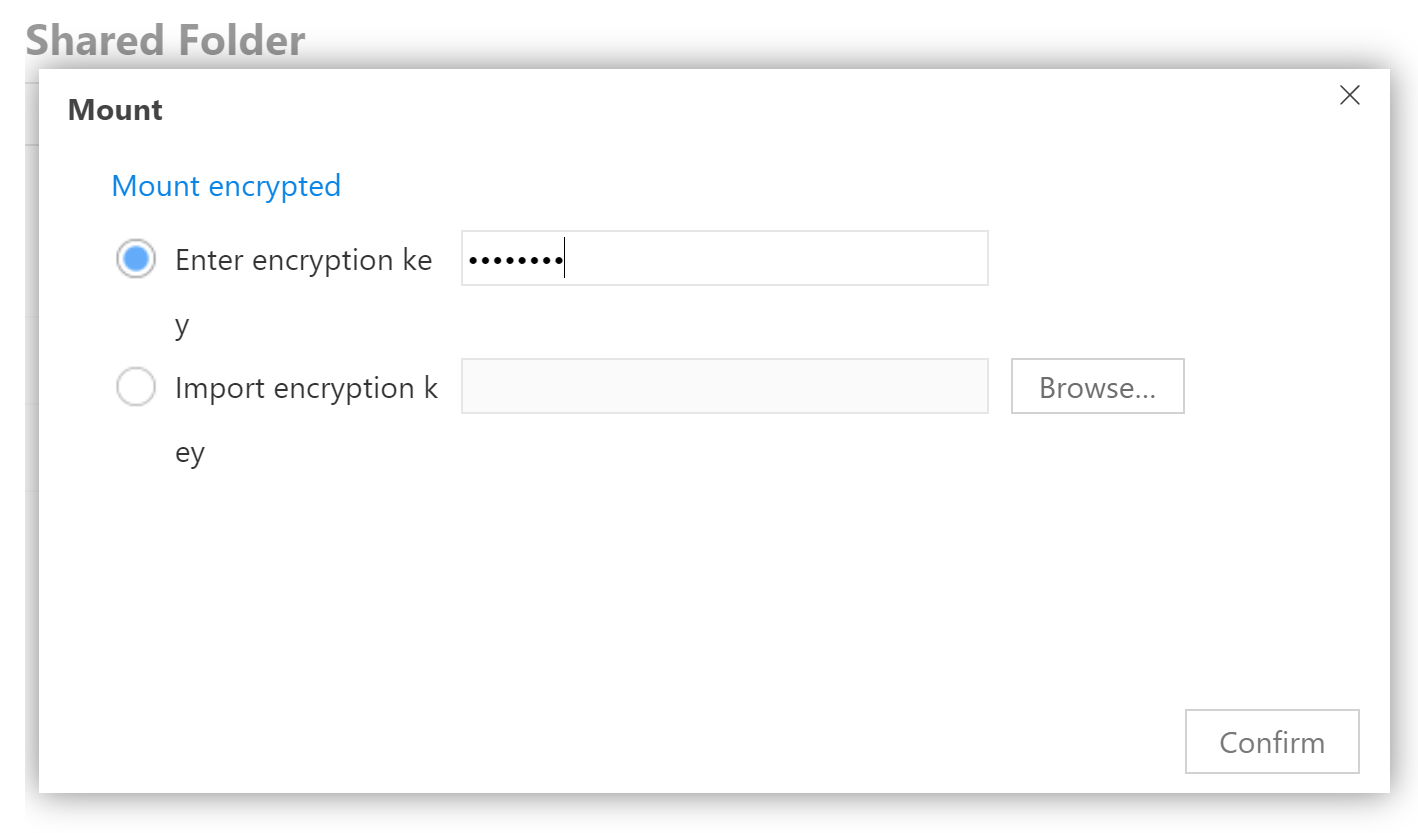
- Mounting with the exported key file.
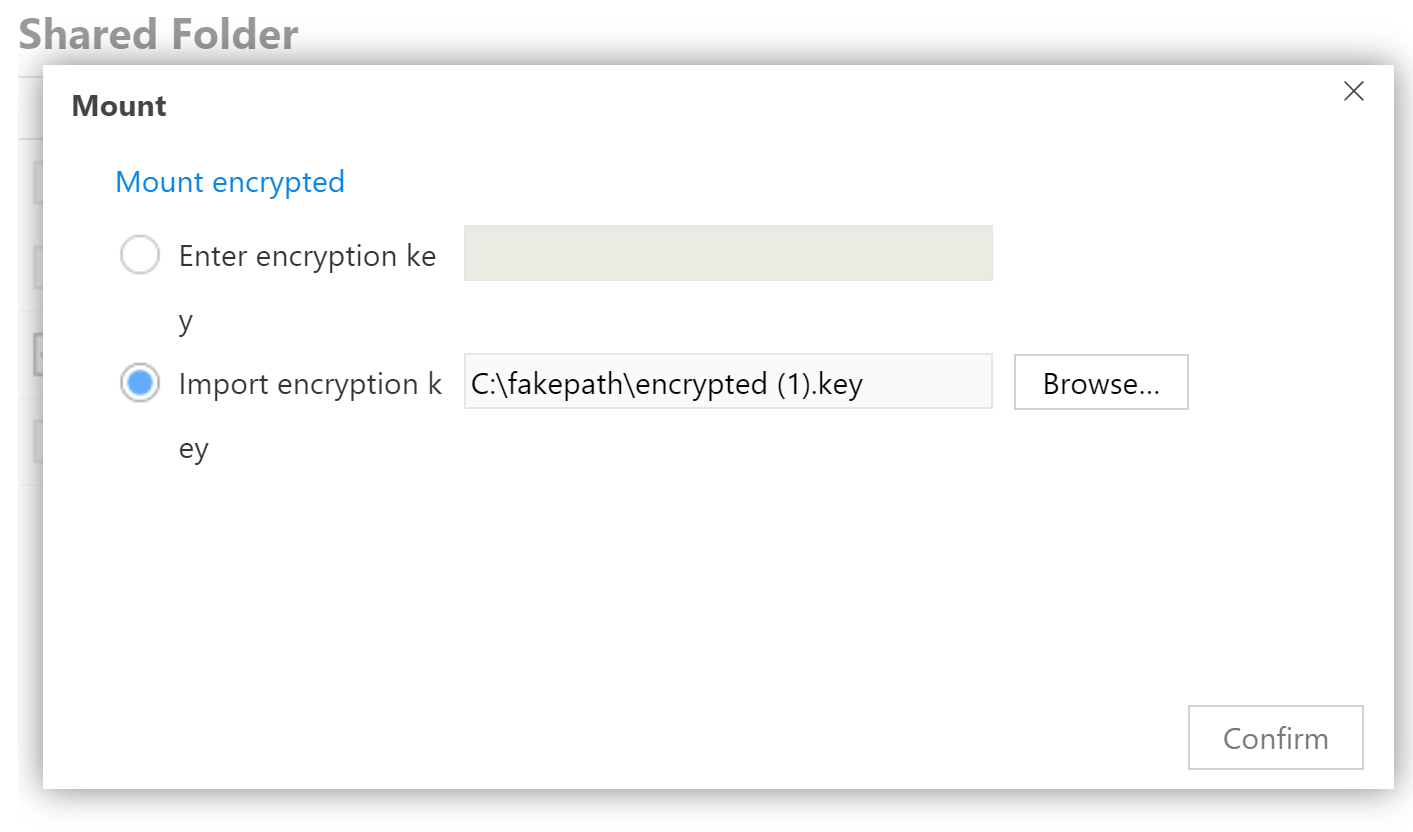
Choosing between these two options, the key file appears to be the more secure one as users can generate a long, random password with high volatility and use that password to produce the backup key file.
Unmounting encrypted shares
Encrypted shares are unmounted automatically once the NAS is powered off or rebooted. Manually unmounting the encrypted share requires accessing the Web UI:

Permanent decryption
Your familiar full-disk encryption tools such as Microsoft BitLocker allow removing the password from an encrypted volume. This is possible because these encryption tools use a concept of separate Media Encryption Keys (MEK, which are used to protect the data) and Key Encryption Keys (KEK, which are used to protect, or “wrap”, the MEK).
TerraMaster does not use the concept of separate MEK and KER. As a result, removing the password is not possible without physically decrypting the entire set of data (which is not supported by TOS). The only way to permanently decrypt the data is removing the encrypted share, re-creating the share without encryption and filling it up with data.
Changing the password: impossible
Decades ago, manufacturers came up with a brilliant idea of separating the binary encryption keys that are used to encrypt and decrypt the data, and secrets that are used to unlock the encryption keys. This wonderful concept allows many things such as using any one of the several different passwords (or multiple types of authentication credentials, such as a smart card or a password) to unlock encrypted volumes. Sadly, this concept is rarely used by NAS manufacturers. TerraMaster is no exception; users cannot change the password because the password itself is the Media Encryption Key.
Manually Decrypting Encrypted Shares
Looking at the path that contains the encrypted files, I wonder if TerraMaster could be inspired by Synology’s implementation of folder-based encryption. The path to encrypted share looks as follows:
/mnt/md0/@encrypted@/
Where “encrypted” is the name of the share (as seen on screenshots above).
Path to decrypted files/mounted share:
/mnt/md0/encrypted/
Since TerraMaster uses eCryptfs, we can use the familiar command to mount the encrypted share:
mount -t ecryptfs /mnt/md0/@encrypted@ /mnt/md0/encrypted
You will need the user’s original, plain-text encryption password. TOS does not appear to be storing the encryption password or the encryption key file anywhere on the disk or in the boot DOM.
If you are able to decrypt the files, but the file names remain encrypted (ECRYPTFS_FNEK_ENCRYPTED), check out the following threads:
Alternatively, this open-source tool: pecryptfs – Portable Userspace eCryptfs may help decrypting individual file names.
What Risks Are Covered by TerraMaster Security Model
Similar to other implementations of NAS encryption, the security model employed by the TerraMaster is stripped down to the bare essentials. I have the following remarks about the TOS security model.
- Unlike volume encryption schemes, folder-based encryption comes with encryption metadata duplicated in every file. “eCryptfs stores cryptographic metadata in the header of each file, so that encrypted files can be copied between hosts; the file will be decrypted with the proper key in the Linux kernel keyring.” (source) This makes secure erase of encrypted data impossible. To securely erase data encrypted with eCryptfs, one must either wipe (overwrite) encryption metadata in each and every encrypted file; wipe the full content of every file; or wipe the entire disk.
- This encryption model does not properly protect the data if one needs to send the disk out for repair/replacement or simply wants to sell the disk. The encryption metadata is duplicated in every file in the encrypted folder. As a result, the attacker can obtain a single file and run a (fast) attack on the encryption key. Open-source tools such as pecryptfs – Portable Userspace eCryptfs may help decrypting individual files.
- The lack of any sort of technical documentation for the data protection scheme is discouraging. This might be passable for the home user and occasional small office use, but unacceptable for anything beyond that.
- The encryption key cannot be changed. Enough said.
Conclusion: TerraMaster Folder Encryption
When it comes to attached storage encryption, we are still in the Stone Age. The lack of basic features, many of which we accept as a given, makes TerraMaster encryption hardly usable. The lack of technical documentation, undocumented functional restrictions and encryption metadata duplicated in every file makes this encryption hardly useful. TerraMaster OS does not separate Media Encryption Keys and Key Encryption Keys, which makes password changes impossible.
The lack of the key management, the inability to change the encryption password, and the inability to encrypt or permanently decrypt existing shares makes TerraMaster NAS encryption one of the least flexible implementations, on par with Thecus NAS encryption. The protection system uses the well-established eCryptfs encryption framework, yet the TOS implementation still lacks transparency or any sort of technical documentation. Security wise, the data would be impossible to decrypt without knowing (or breaking) the user’s encryption password (or, alternatively, without access to the exported encryption key).
At the same time, TOS encryption implementation is straightforward enough to appeal to some users. However, those same users may be put off by the need of re-entering their encryption password in the Web interface every time they power on or reboot the NAS.
Post a Comment